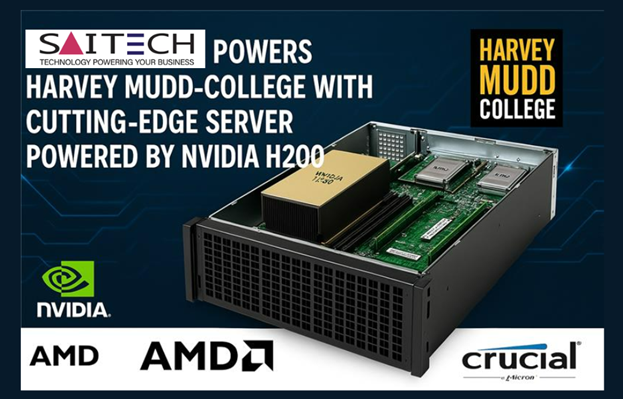
Saitech Inc. Powers Harvey Mudd College with Cutting-Edge Server Powered by NVIDIA H200
Saitech Inc. is proud to support Harvey Mudd College with a custom-built high-performance computing server, featuring the powerful NVIDIA H200 GPU. Designed to enhance the college’s AI research and HPC projects, this tailored server is optimized for deep learning, scientific simulations, and complex data analytics. Powered by cutting-edge NVIDIA, AMD, and Crucial technologies, the server is set to drive innovation and accelerate breakthroughs in AI and computational science. As a trusted NVIDIA partner, Saitech Inc. delivers top-tier performance with fully integrated, purpose-built solutions to meet the unique needs of academic institutions like Harvey Mudd College.